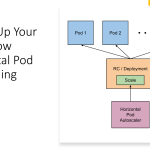
In this continuation blog, we will explore some more advanced topics related to DevSecOps implementation.
Threat Modeling
Threat modeling is the process of identifying potential threats to an application or system and evaluating their impact. It helps identify potential security vulnerabilities and prioritize security activities. The following steps are involved in the threat modeling process:
- Identify assets: Identify the assets that need to be protected, such as data, applications, and infrastructure.
- Identify threats: Identify potential threats to the assets, such as unauthorized access, data breaches, and denial of service attacks.
- Analyze risks: Analyze the risks associated with the identified threats and prioritize them based on the severity of their impact.
- Mitigate risks: Develop and implement controls to mitigate the identified risks.
Continuous Compliance
Compliance is an essential aspect of security. DevSecOps requires continuous compliance monitoring to ensure that the software and infrastructure comply with security policies and regulatory requirements. The following activities are involved in continuous compliance:
- Define compliance requirements: Define the compliance requirements for the software and infrastructure based on the regulatory and industry standards.
- Implement compliance controls: Implement controls to ensure compliance with the defined requirements.
- Monitor compliance: Monitor the software and infrastructure continuously to ensure that they comply with the defined requirements.
- Remediate non-compliance: Remediate any non-compliance issues as soon as they are identified.
Chaos Engineering
Chaos engineering is the process of intentionally introducing failures into the system to identify potential vulnerabilities and improve its resiliency. It involves the following steps:
- Define the scope: Define the scope of the chaos engineering exercise, such as the specific system components to be tested.
- Plan the experiment: Plan the experiment by defining the failure scenarios to be introduced and the metrics to be monitored.
- Conduct the experiment: Conduct the experiment by introducing the failure scenarios and monitoring the system’s behavior.
- Analyze the results: Analyze the results of the experiment to identify potential vulnerabilities and areas for improvement.
Conclusion
DevSecOps is a critical practice that requires continuous improvement and refinement. By implementing threat modeling, continuous compliance, and chaos engineering, organizations can improve their security posture significantly. These practices help identify potential vulnerabilities, ensure compliance, and improve system resiliency. By following these best practices, organizations can build and deploy software that is secure, compliant, and resilient.