Continuing from my previous blog, let’s explore some more advanced topics related to DevSecOps implementation.
Threat Intelligence
Threat intelligence is the process of gathering information about potential threats and vulnerabilities to an organization’s systems and applications. It involves collecting, analyzing, and disseminating information about potential threats, vulnerabilities, and threat actors. Threat intelligence includes the following activities:
- Collection: Collect information about potential threats from various sources, such as social media, security vendors, and security researchers.
- Analysis: Analyze the collected information to identify potential threats and vulnerabilities.
- Dissemination: Disseminate the analyzed information to relevant stakeholders, such as security teams, system administrators, and executives.
- Response: Develop and implement response plans to mitigate identified threats and vulnerabilities.
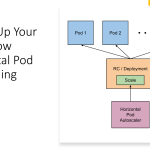
Container Security
Containers have become a popular way to deploy and manage applications in a DevSecOps environment. However, they also introduce new security challenges. Container security includes the following activities:
- Image Scanning: Scan container images for vulnerabilities before deployment to ensure that they do not introduce potential security risks.
- Access Control: Control access to containers to ensure that only authorized users and processes can access them.
- Runtime Security: Monitor container runtime behavior to detect potential security issues, such as unauthorized access and malicious activity.
- Compliance: Ensure that container deployment and management comply with regulatory requirements and security policies.
Serverless Security
Serverless computing is a way to deploy and manage applications without the need for managing infrastructure. However, it also introduces new security challenges. Serverless security includes the following activities:
- Access Control: Control access to serverless functions to ensure that only authorized users and processes can access them.
- Data Protection: Protect sensitive data processed by serverless functions using encryption and access control mechanisms.
- Runtime Security: Monitor serverless function runtime behavior to detect potential security issues, such as unauthorized access and malicious activity.
- Compliance: Ensure that serverless deployment and management comply with regulatory requirements and security policies.
Conclusion
DevSecOps is a critical practice that requires continuous improvement and refinement. By implementing threat intelligence, container security, and serverless security, organizations can improve their security posture significantly. These practices help gather information about potential threats and vulnerabilities, secure container and serverless environments, and ensure compliance with regulatory requirements and security policies. By following these best practices, organizations can build and deploy software that is secure, compliant, and efficient in a DevSecOps environment.