This is a final series to conclude and summarize the key topics covered in previous 8 blogs:
DevSecOps is an approach to software development that emphasizes integrating security into every stage of the software development lifecycle. Application security and immutable infrastructure are two key practices that can help organizations achieve this goal.
Application Security
Application security involves the process of identifying, analyzing, and mitigating security vulnerabilities in software applications. By implementing application security practices, organizations can reduce the risk of security breaches, ensure compliance with regulatory requirements, and protect customer data.
One key aspect of application security is threat modeling. Threat modeling involves identifying potential threats and vulnerabilities in the application design, such as SQL injection or cross-site scripting. By identifying these threats early in the development process, organizations can take steps to mitigate them and reduce the risk of security breaches.
Another key aspect of application security is security testing. Security testing involves testing the application for potential security vulnerabilities, such as buffer overflow or input validation issues. Organizations can use a variety of tools and techniques for security testing, including penetration testing, fuzz testing, and code review.
Once potential security vulnerabilities are identified, organizations can take steps to remediate them. This may involve using automated scripts or manual processes to fix the code, or in some cases, rewriting the application code entirely. By remediating security vulnerabilities, organizations can reduce the risk of security breaches and protect their customers.
Immutable Infrastructure
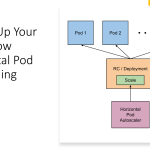
Immutable infrastructure is a practice that involves treating infrastructure as an immutable entity that cannot be modified once it is deployed. This practice ensures that the infrastructure remains consistent and predictable, reducing the risk of configuration errors and enhancing the reliability and security of the infrastructure.
Immutable infrastructure can be achieved through a variety of techniques, including containerization, virtualization, and infrastructure as code. These techniques enable organizations to create and manage infrastructure as code, making it easier to automate and scale infrastructure deployments.
One key benefit of immutable infrastructure is enhanced security. By treating infrastructure as immutable, organizations can ensure that the infrastructure is free from vulnerabilities and that changes are traceable and auditable. This reduces the risk of security breaches and makes it easier to comply with regulatory requirements.
Another key benefit of immutable infrastructure is scalability. Immutable infrastructure enables organizations to scale their infrastructure more efficiently, since infrastructure deployments can be automated and managed as code. This reduces the time and effort required to deploy and manage infrastructure, freeing up resources for other tasks.
In conclusion, application security and immutable infrastructure are two key practices that can help organizations achieve the goals of DevSecOps. By implementing application security practices, organizations can reduce the risk of security breaches, ensure compliance with regulatory requirements, and protect customer data. By implementing immutable infrastructure practices, organizations can enhance the reliability and security of their infrastructure, reduce the risk of configuration errors, and scale their infrastructure more efficiently.
Now, let’s summarize the key points of all the topics covered in earlier blogs in a final blog:
DevSecOps: A Summary of Key Topics
DevSecOps is an approach to software development that emphasizes integrating security into every stage of the software development lifecycle. Some key topics related to DevSecOps include:
- Continuous Integration and Continuous Deployment: CI/CD is a practice that involves automating the build, test, and deployment process to improve the speed and reliability of software development.
- Configuration Management: Configuration management is a practice that involves managing infrastructure and application configurations to ensure consistency and reduce the risk of configuration errors.
- Continuous Compliance: Continuous compliance involves automating the process of ensuring compliance with regulatory requirements, such as HIPAA or GDPR.
- Threat Intelligence: Threat intelligence involves collecting, analyzing, and disseminating information about potential security threats to an organization.
- Application Security: Application security involves the process of identifying, analyzing, and mitigating security vulnerabilities in software applications.
- Immutable Infrastructure: Immutable infrastructure involves treating infrastructure as an immutable entity that cannot be modified once it is deployed. This practice ensures that the infrastructure remains consistent and predictable, reducing the risk of configuration errors and enhancing the reliability and security of the infrastructure.
- Implementing these practices can help organizations achieve the goals of DevSecOps, including reducing the risk of security breaches, improving compliance with regulatory requirements, and enhancing the reliability and scalability of their software development process.
Here’s a summary of the benefits of each of these practices:
In conclusion,
DevSecOps is a holistic approach to software development that prioritizes security at every stage of the software development lifecycle. By integrating security into the software development process, organizations can minimize security risks and vulnerabilities, improve compliance with regulatory requirements, and enhance the overall reliability and scalability of their software.
To achieve these goals, DevSecOps emphasizes the implementation of various practices, including continuous integration and continuous deployment, configuration management, continuous compliance, threat intelligence, application security, and immutable infrastructure. Each of these practices plays a critical role in enhancing the security and reliability of the software development process and reducing the risk of security breaches and vulnerabilities.
Continuous integration and continuous deployment enable faster and more reliable software development, while configuration management ensures consistency and reduces the risk of configuration errors. Continuous compliance ensures that software development complies with regulatory requirements, while threat intelligence enhances the organization’s awareness of potential security threats. Application security minimizes security risks and vulnerabilities, while immutable infrastructure enhances security and reliability, making it easier to scale up or down as necessary.
In summary, DevSecOps is a critical approach to software development that prioritizes security throughout the software development lifecycle. By implementing best practices and embracing a culture of security, organizations can minimize security risks and vulnerabilities, improve compliance with regulatory requirements, and enhance the reliability and scalability of their software development process.